Cyber crimes are on the rise. You don’t have to be invested in tech news to a very great degree to know that. With the advancement of technology, the danger of it backfiring—in case it landed in the wrong hands—has been thoroughly consistent. With more and more business (both public and private sector) moving online the amount of damage an infiltration could cause has been directly proportional.
The US energy department has come under the cloud of a cyber attack. Symantech, the group that provides advanced solutions to data loss and malware and hacking, identified Dragonfly’s ongoing cyberespionage campaign activity.
The energy sector has become an area of increased interest to cyber attackers over the past two years. Most notably, disruptions to Ukraine’s power system in 2015 and 2016 were attributed to a cyber attack and led to power outages affecting a large chunk of the population. In recent months, there have also been media reports of attempted attacks on the electricity grids in some European countries, as well as reports of companies that manage nuclear facilities in the U.S.
Hacker group Dragonfly targets US energy sectors
The previous series of cyber attacks initiated by Dragonfly was from 2011 to 2014. After Symantech bought forth their involvement, the hacking group went on a hiatus until December of 2015.
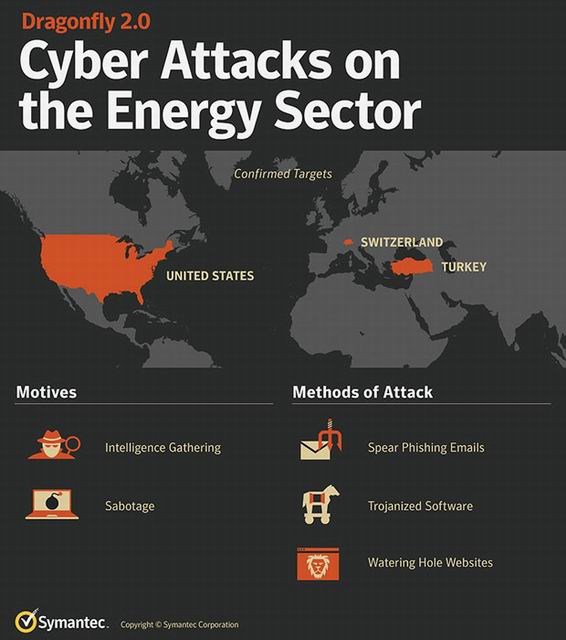
The first attack this time around disguised itself as an email invitation to the company employees for a New Years Eve’s party. They are employing similar tactics as their last attacks, using waterhole attacks, malicious email, and Trojanized software.
Symantech has pointed out their activity concentrations in US-Turkey and Switzerland. The group seems to want to learn how these energy sectors operate and most likely has the ability to make changes and remotely control it if it decides to do so. Symantech said that all of their customers are protected against anything the cyber hackers could throw at them.
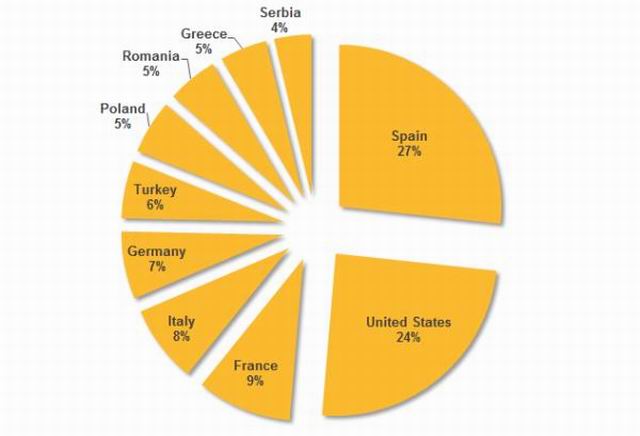
Among the targets of Dragonfly were energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment providers. The majority of the victims were the United States, Spain, France, Italy, Germany, Turkey, and Poland.
Experts claim that Dragonfly is equipped with capabilities to compromise third party websites while launching cyberespionage from various vector simultaneously. They are well resourced with malware. While their initial target were US defensive and aviation companies their sole focus has been shifted to the power sector.
Although there is no one switch that would take away all the electricity of the US it still does not void the gravity of the situation.
Indegy’s Tamir maintained that Dragonfly is not only trying to steal information but compromise systems. The analysts are still unclear as to what is the basic motivation for the group at this point.
“The sophistication of the attack, the targets of the attack, the gathering of information indicates there’s a bigger play here that’s more typical of a nation-state than a criminal organization,” said Symantech’s Chen.
Dragonfly has used only two malwares in it’s frontal attacks. Oldrea and Trojan.Karagany. while the later was available on the underground market the former is believed to be made either by the group itself or created for it.
Oldrea allows the hacker to extract the data files and command and control (C&C) from a remote site. Trojan.Karagany is Karagany is capable of uploading stolen data, downloading new files, and running executable files on an infected computer. It is also capable of running additional plugins, such as tools for collecting passwords, taking screenshots, and cataloging documents on infected computers.
IBM has identified increasing cyber attacks. There were 2,788 attacks in 2016, up from 640 attacks in 2013, for instance. That trend appears to be continuing this year. Through July, IBM already had reported 2,522 attacks.
Tamir said that these attacks are not unmanageable but the power sector is moving too slow to cope with it.




